In this page we try to explain common procedures and features that can be complex and hard to grasp for newcomers.
Some are related to Hawkpost directly, but others are related to PGP and associated tasks and tools.
Of course we can't cover all the surface or explicitly address all questions in this document. So if your question isn't here feel free to drop a line through our support channels, and we'll try to help you as soon as possible.
- Ask the instance administrator through email: pjaneiro@whitesmith.co
- Chat with the development team on IRC. The channel is #hawkpost on freenode
- Open an issue on the project board with your question
HOW TO SETUP HAWKPOST
In order to start using Hawkpost as a user that receives confidential information, you have to fill certain requirements, such as:
- Provide a PGP public key
- Provide your key's fingerprint
- Have the required software to decrypt the messages
If you don't know how to fulfill the first and third point, please check the next section. Otherwise the configuration is quite simple.
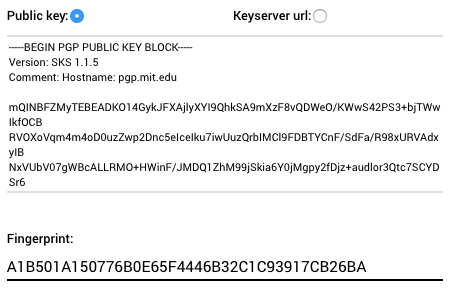
As you can see in the above figure, you just have to fill the public key field and the matching fingerprint. After this you're ready to go. We strongly recommend to also fill your personal data (as name) so it can show up on the submission page.
To find your key's fingerprint, you can run the following command if you're using Gnu Privacy Guard (GPG):
gpg --fingerprint <key id or email>
If you're using a graphical tool, you can generally find this info on the key properties section of your tool.
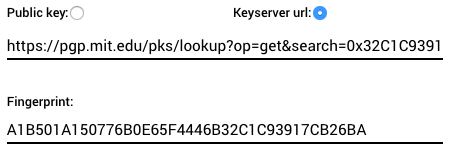
For extra security and features you can specify the keyserver URL of your key instead of providing it directly. This way the system will fetch the key and regularly check that URL for key updates and the system will stop allowing submissions to your boxes once the key is revoked or expired (the fingerprint is always required).
HOW TO GENERATE A PGP KEY
Hawkpost works with an encryption technology known as PGP. So to create boxes you'll need to setup a PGP key pair and provide us the public part/key. If you already have one, this section is not for you.
Since Hawkpost works only through email, the easiest way to setup a key pair is using your email client, or through a compatible plugin/extension in case the email client doesn't support PGP natively. There are various articles in the Internet about this topic, so it's easy to find some that match your specific setup.
As an example, in the next paragraphs we point to some tutorials addressing popular email clients.
For webmail users, one tool that is very useful is Mailvelope. This browser extension allows you to easily open the encrypted messages, and also to generate your keys. An introductory tutorial can be found here.
For Thunderbird users, the common practice is to install a plugin called Enigmail, which like Mailvelope, will allow you to decrypt Hawkpost messages, and manage your keys as well. An introduction can be found here.
Check this video for an Outlook tutorial and this guide for the case of Apple Mail.